A command-and-control [C&C] server is a computer controlled by an attacker or cybercriminal which is used to send commands to systems compromised by malware and receive stolen data from a target network. Attacker uses a malicious server to command and control already compromised machines over a network. The malicious server (the command and control server) is also used to receive the desired payload from the compromised network. This is typically done through compromised channels ( like malvertising, vulnerable web browser plugins, phishing, installation of malware etc.). Companies often use a list of C&C domains, URLS and IP addresses from threat intelligence providers and import them in SIEM solutions for alerting on systems that are connected to these C&C Systems.
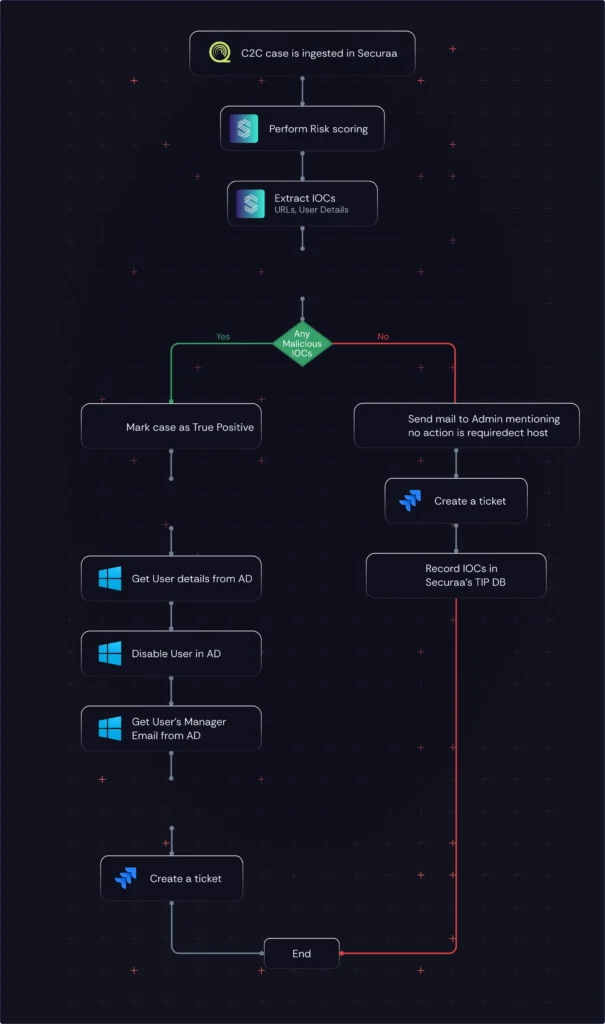
Securaa streamlines response by automating standard procedures for Command-and-Control detections.
Incidents are pulled from SIEM, and IOCs like IPs are extracted for analysis.
IP addresses are validated using Securaa’s TIP and external threat intelligence tools.
Securaa maps the incident to the involved user using details from the ingested alert.
Suspicious users are blocked in AD and malicious IPs are blacklisted in firewalls.
See how we can help, live and in real time.
Talk With Our Team
See how we can help, live and in real time.