The Challenge: Why Alert Fatigue Hurts SOC Teams
Security operations teams face a fundamental problem: alert overload. Our analysis shows that security analysts receive hundreds of technical alerts daily, with a single incident generating 50+ individual alerts across multiple tools. Each alert contains fragments of information—IP addresses, timestamps, system logs, and technical indicators—scattered across SIEM, EDR, firewall, and other security platforms.
The result? Analysts spend 30-45 minutes per incident performing manual correlation, delaying critical response decisions. This isn’t just inefficient—it’s dangerous. While analysts piece together what’s happening, threats continue to spread.
What is Incident Summarization?
The Incident Summarization Agent is an AI-powered system that instantly analyzes all related security data and generates clear, contextual summaries tailored for different stakeholders. It transforms raw technical data into structured intelligence that answers three critical questions:
- What happened?
- What’s the impact?
- What should we do?
This isn’t simple alert aggregation. It’s intelligent analysis that understands context, recognizes patterns, and provides actionable recommendations based on your specific environment.
How Does an Incident Summarization Agent Work?
When an alert triggers, the Incident Summarization Agent executes a three-phase process:
Phase 1: Comprehensive Data Collection
The agent immediately pulls information from:
- SIEM platforms for security events
- EDR solutions for endpoint behaviors
- Firewall and proxy logs for network traffic
- Threat intelligence feeds for IP/domain reputation
- Identity systems for user context
It correlates alerts using multiple factors: IP addresses, timestamps, behavioral patterns, and user activities to build a complete picture of the incident.
Phase 2: Advanced Pattern Analysis
The agent performs automated analysis across five dimensions
| Dimension | Analysis |
| Pattern Recognition | Identifies specific attack techniques (C2, lateral movement, exfiltration) |
| Reputation Analysis | Validates indicators against multiple threat intelligence sources |
| Scope Assessment | Maps all affected internal systems and potential blast radius |
| Impact Analysis | Determines data exposure risk and business impact |
| Confidence Scoring | Calculates verdict reliability based on evidence strength |
Phase 3: Contextual Summary Generation
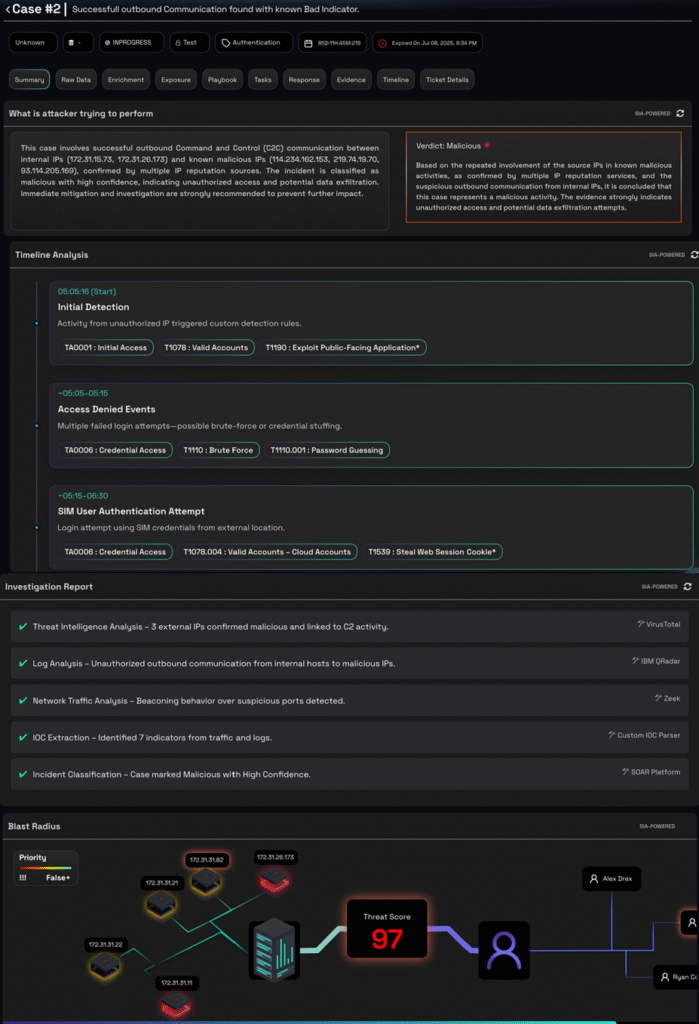
Based on the analysis, the agent generates role-appropriate summaries. Here’s a real example from a Command C Control detection:
Technical Summary for SOC Analysts
CASE SUMMARY – COMMAND & CONTROL DETECTED Case ID: INC-2024-7823
Verdict: Malicious Confidence: High (94%)
ATTACK DETAILS:
This case involves successful outbound Command and Control (C2C) communication between
internal IPs (172.31.15.73, 172.31.26.173) and known malicious IPs (114.234.162.153,
219.74.19.70, 93.114.205.169), confirmed by multiple IP reputation sources.
TECHNICAL INDICATORS:
- C2 Protocol: HTTPS over port 443
- Beacon Interval: Every 3600 seconds
- Data Transferred: 2.3GB outbound
- Persistence Method: Scheduled task identified
- Affected Systems: 3 workstations, 1 server
IMMEDIATE ACTIONS REQUIRED:
- Block malicious IPs at firewall
- Isolate affected internal systems
- Capture memory dump for forensics
- Review all traffic from internal IPs
What Are the Key Benefits?
- Translates complex technical indicators into clear, audience-appropriate language while maintaining accuracy.
- Preserves critical forensic details and regulatory requirements for investigations and compliance.
- Correlates security events, identifies root cause vs. symptoms, and recognizes known attack patterns.
- Provides contextual intelligence with historical data and highlights time- sensitive actions.
At Securaa, we deliver next-gen SOAR solutions that empower security teams to cut through alert fatigue and respond faster with AI-driven incident summarization, automation, and orchestration. Contact us today to discover how we can help your SOC stay ahead of evolving cyber threats.